We’ve already guided you through Phase I of registration for the NPC’s Data Privacy Act. If you’ve completed that successfully, you should eventually receive an email for your access code to Phase II. Here is what it looks like:
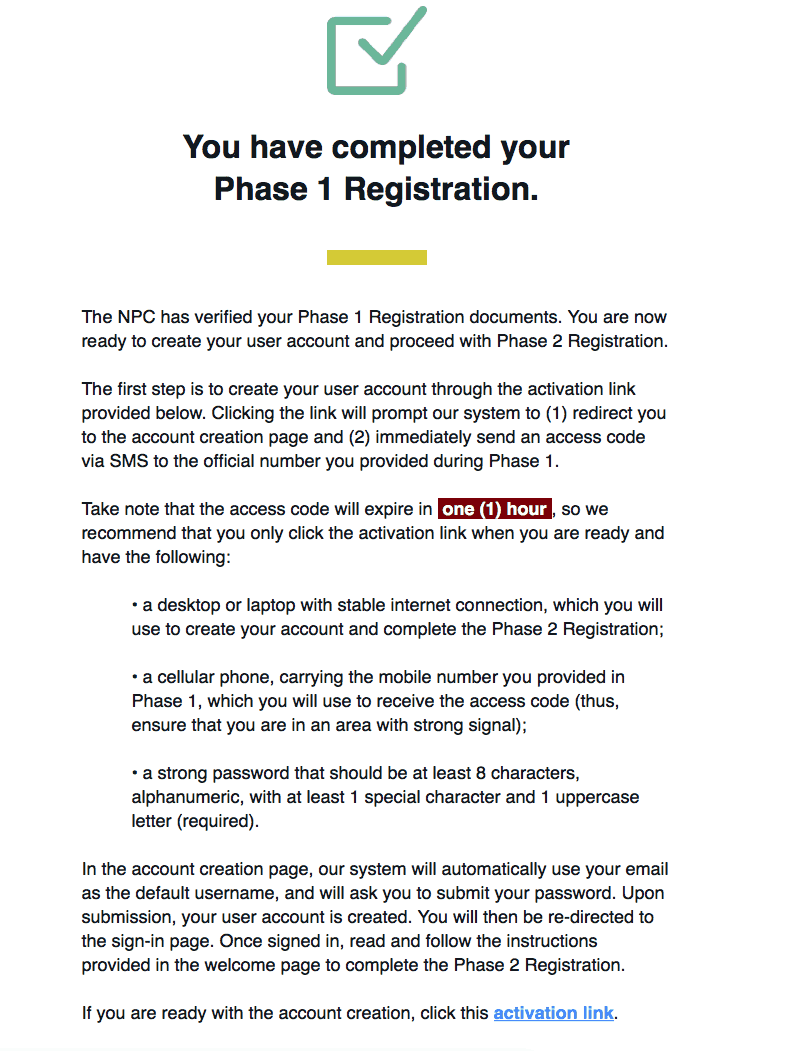
As you read from the image above, clicking on the activation link will send you a code via SMS. However, there have already been reports of this failing to send in some cases. Some cases have also seen people getting an SMS but being told that it has already expired after they try using the code in it.
If either of these things happens to you, don’t panic. All you have to do is call the NPC to request a working code. In our own case, we went to their office personally to ask for the activation SMS.
After You Get the Access/Activation Code
That access code will send you to Phase II of the registration webpage. This is when you basically tell the NPC all relevant details of your data processing system. It’s not very complicated: you will just have to fill in a simple electronic form.
Here are some of the items you’ll be answering at this stage, as well as the right answers to them if you’re a SeriousMD user:
1. What should you put under the DPS name?
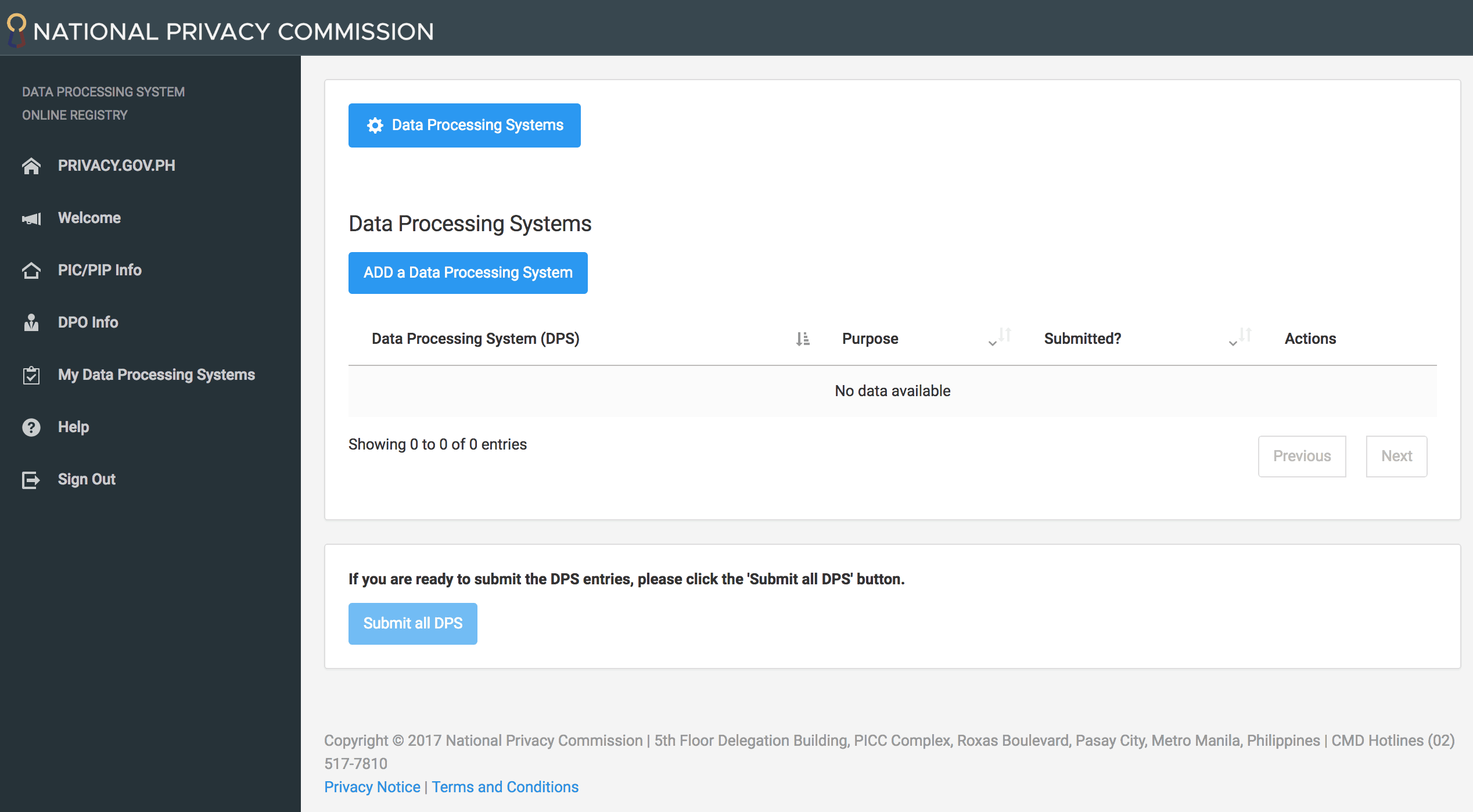
ANSWER: Just name it something like “for patient consultation” or anything along those lines.
2. Should you pick PIC or PIP?
ANSWER: Pick PIC IF SeriousMD is the only processor you use. If you still keep manual records, then you’ll need to select Both as you will be the PIP for that.
3. Should you select Automated Decision Making (if you chose Electronic under “Type of DPS”)?
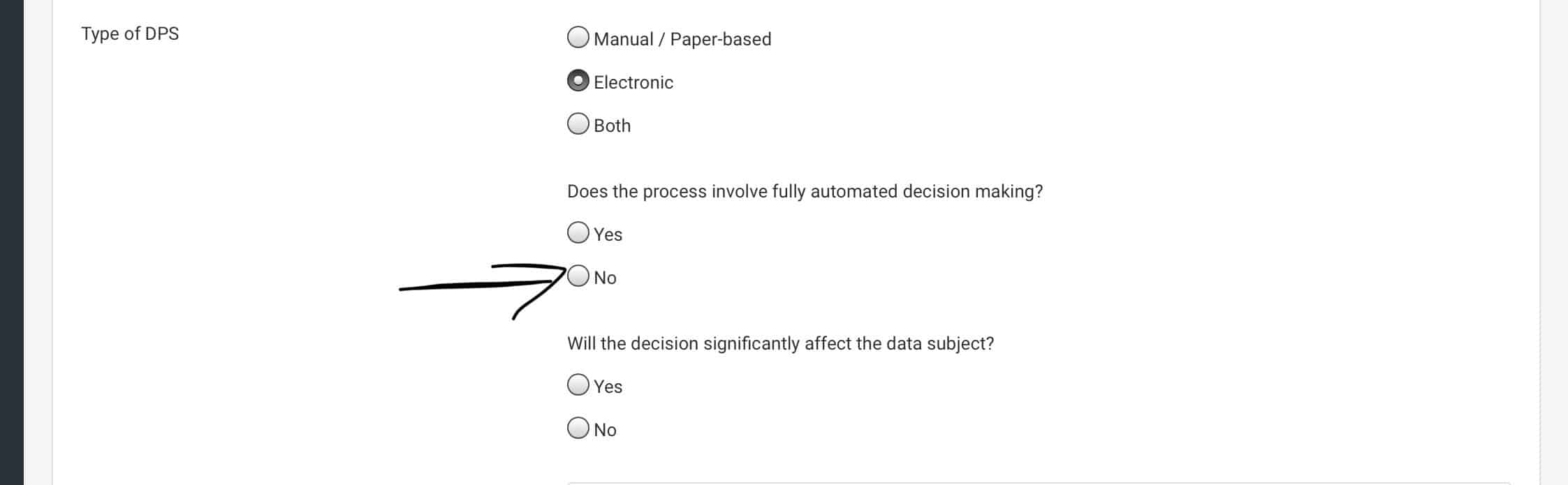
ANSWER: No.
4. Will the decision significantly affect the data subject (again, a question that comes up after you choose the Electronic option under “Type of DPS”?
ANSWER: No.
5.What should I put under “Purpose”?
ANSWER: Just state that it’s for patient registration, consultation and scheduling. Please state clearly if you use it for your personal research and if you submit that research to somewhere else.
6. Is the system outsourced and is there a subcontracting agreement?
ANSWER: Yes and yes.
7. Will personal information be transferred outside the Philippines?
ANSWER: Yes. If you are using another information processor, you may have to check first.
That should take care of the more confusing parts, so just hit save afterwards. The rest is straightforward. The NPC has a pretty concise guide to what other information it will demand for Phase II. To be exact, you’ll find the text below on its site.
As per IRR of Data Privacy Act 2012 Sec. 47, the contents of registration shall include:
- The name and address of the personal information controller or personal information processor, and of its representative, if any, including their contact details;
- The purpose or purposes of the processing, and whether processing is being done under an outsourcing or subcontracting agreement;
- A description of the category or categories of data subjects, and of the data or categories of data relating to them;
- The recipients or categories of recipients to whom the data might be disclosed;
- Proposed transfers of personal data outside the Philippines;
- A general description of privacy and security measures for data protection;
- Brief description of the data processing system;
- Copy of all policies relating to data governance, data privacy, and information security;
- Attestation to all certifications attained that are related to information and communications processing; and Name and contact details of the compliance or data protection officer, which shall immediately be updated in case of changes.
In short, among other things, you will need to supply these:
- The name and address of the PIC/PIP
- Why you’re collecting or handling others’ personal data
- If you have a third party doing the data processing for you
- The types of people whose data you collect and the types of data you collect from them
- The people with whom you share the data
- (If applicable) an explanation for why you might send that data out of the country
- How your data processing system works
- What your policies are on everything data-related
- (If applicable) proof of certifications you have in data protection
Most of these are actually covered in your average organization’s privacy manual. Items 7 and 8 in particular can be fulfilled by such a document. As such, you might want to create such a guide as early as now. It would take care of a lot of questions that people (or even the NPC) might pose to you eventually.
Creating a Privacy Manual
The NPC has a detailed guide to this, complete with examples for most sections. If you have trouble understanding its contents or just can’t be bothered to read all of them, we present a synopsis here.
First, this is what your privacy manual’s Table of Contents should look like:
- Introduction
- Definition of Terms
- Scope and Limitations
- Processing of Personal Data
- Security Measures
- Breach and Security Incidents
- Inquiries and Complaints
- Effectivity
- Annexes
Need a longer but still bite-sized explanation for all of these? Here you go:
1. Introduction – Where you give a synopsis of related laws, specifically the Data Privacy Act of 2012, and state your commitment to their principles. This is basically where you explain why a privacy manual is necessary.
2. Definition of Terms – A glossary of terms relating to data protection, e.g. data subject, personal information, (data) processing, personal information processor, etc.
3. Scope and Limitations – Where you state whose activities are covered by the manual. Usually, this means every member of your organization.
4. Processing of Personal Data – Where you describe the many ways data is used or passed on in your organization. This includes the way you collect it, why you collect it, how you store and dispose of it, who can access it, and how/to whom you may share it.
Thus, you can divide this section into 5 subsections: Collection, Use, Storage/Retention/Destruction, Access, and Disclosure/Sharing.
5. Security Measures – Where you describe the security measures you take to safeguard data. You can divide these in the organization security measures, physical security measures, and technical security measures.
a. Organization Security Measures
- The name of your Data Protection Officer (DPO) or Compliance Officer for Privacy (COP)
- The responsibilities of the DPO or COP
- How you inform employees of your policy and procedures on data privacy (e.g. training, seminars, etc.) and how often you do it
- How often you conduct Privacy Impact Assessment
- What (if any) activities the DPO or organization takes to ensure compliance with its data privacy policy
- Whether or not employees have to sign a nondisclosure agreement
- How often the privacy manual itself is evaluated or updated
b. Physical Security Measures
- What format the data is in
- What type of storage is used to keep it and where the storage is
- Which personnel can access the data storage
- How you keep track of who accesses the data
- If applicable, how your office’s space is designed to consider data privacy (e.g. if work stations have barricades or space between them)
- What persons involved in processing data should do and any steps they take to limit data breach (e.g. not bringing recording devices into the data storage room)
- What methods are or are not used by the organization to transfer data either internally or to a third party
- How long your organization stores data (e.g. for one year)
- How you dispose of data
c. Technical Security Measures
- How you monitor for security breaches
- What security measures are already in the data storage/processing application (e.g. encryption, password-protection, etc.)
- How you test the effectiveness of the security measures
- How often you test the effectiveness of the security measures
6. Breach and Security Incidents – Where you describe your procedures for dealing with a data breach. This includes things like explaining who gets assigned to investigate, how they shall notify the concern data subject, what steps they should take in documenting their progress, etc.
7. Inquiries and Complaints – Where you explain how data subjects can send either questions or complaints about how you process their data. Be sure to include the proper contact details, e.g. an email address for data complaints and your usual response policy (how long it takes you to answer).
8. Effectivity – Where you state the period when this manual is in effect, e.g. 1 January 2018 to 1 January 2019.
9. Appendices – Where you add other organization documents that might be relevant, e.g. inquiry forms, complaint forms, etc.
And that’s it. If you need more help, we’re happy to provide it to all our users. We’re even giving out a privacy manual template and DPA registration checklist for free.
That means you won’t have to see a consultant just to develop your organization’s formal privacy policy: all you have to do is replace the blanks in our template with your organization’s name and other specifics, and presto! You have a viable privacy manual. You’ll also be able to complete DPA registration with ease if you have our checklist.
Want the Free Privacy Manual Template and DPA Registration Checklist?
You’ll get it if you’re already one of our users. If not, all you have to do is subscribe to SeriousMD Pro or Business. Once you’re one of the many doctors now subscribed and using the app, all you need to do is contact Support to get these extremely convenient freebies.

